Fluxion (linset)
I hadn't ventured into Hackforums since a while, and this time when I went there I saw a thread about a script called Fluxion. It's based on another script called linset (actually it's no much different from linset, think of it as an improvement, with some bug fixes and additional options). I did once think about (and was asked in a comment about) using something like a man in the middle attack/ evil twin attack to get WPA password instead of going the bruteforce/dictionary route, but never looked the idea up on the internet nor spent much time pondering over it. However, once I saw the thread about this cool script, I decided to give it a try. So in this post I'll show you how I used Fluxion, and how you can too.Disclaimer : Use this tool only on networks you own .Don't do anything illegal.
Contents
- Checking if tool is pre-installed, getting it via github if it isn't.
- Running the script, installing dependencies if required.
- Quick overview of how to use Fluxion.
- Detailed walk-through and demonstration with text explanation and screenshots
- Video demonstration (not identical to the written demo, but almost the same)
- Troubleshooting section
Just double checking
 The first thing I did was make sure that Kali doesn't already have this tool. Maybe if you are reading this post a long time after it was written, then you might have the tool pre-installed in Kali. In any case, try this out:
The first thing I did was make sure that Kali doesn't already have this tool. Maybe if you are reading this post a long time after it was written, then you might have the tool pre-installed in Kali. In any case, try this out:fluxionI, personally tried to check if linset or fluxion came pre-installed in Kali (though I didn't expect them to be there).
Getting the script
Getting the script is just a matter of cloning the github repository. Just use the git command line tool to do it.
git clone https://github.com/deltaxflux/fluxion
Update : There seems to be some legal trouble with Fluxion. The creator of the script has removed the source code of the tool, and uploaded code that is supposed to delete fluxion from your computer. I don't know the specifics of what is going on, but will provide updates ASAP.
Update 2: Now the repository is gone altogether!
What this means : As of now, this tutorial is useless. If you can find the source code for Fluxion, then you can use it and continue with the tutorial. Otherwise, not much can be done without the tool.
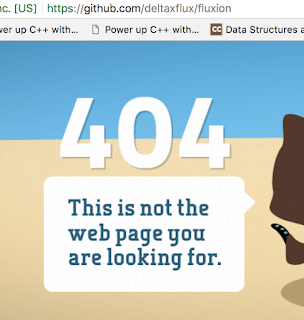
Update 3!
You can try this repo - https://github.com/wi-fi-analyzer/fluxion. It's an old version, might or might not work.
If you have any problems with this step, then you can just naviagate to the repostitory (updated link) and manually download the stuff.

git clone https://github.com/wi-fi-analyzer/fluxion
Update 4
<!--Update_begins-->
Now you can find the latest version of Fluxion here. There shouldn't be any further issues at all.-
git clone https://github.com/FluxionNetwork/fluxion
<!--Update_ends-->
 |
| There are 4 dependencies that need to be installed |
Running the script
Just navigate to the fluxion directory or the directory containing the scripts in case you downloaded them manually. If you are following the terminal commands I'm using, then it's just a simple change directory command for you:
cd fluxionNow, run the script.
sudo ./fluxion
Dependencies (for older version)
If you have any unmet dependencies, then run the installer script.sudo ./Installer.sh
 I had 4 unmet dependencies, and the installer script run was a buggy experience for me (though it might be becuase I have completely screwed up my system, editing files I wasn't supposed to and now I can't get them back in order) .It got stuck multiple times during the process, and I had to ctrl+c my way out of it many times (though ctrl+c didn't terminate the whole installer, just the little update popup). Also, I ran the installer script twice and that messed up with some of the apt-get settings. I suggest that after installation is complete, you restore your /etc/apt/sources.list to it's original state, and remove the bleeding edge repositories (unless you know what you're doing). To know what your repository should look like, take a look here.
I had 4 unmet dependencies, and the installer script run was a buggy experience for me (though it might be becuase I have completely screwed up my system, editing files I wasn't supposed to and now I can't get them back in order) .It got stuck multiple times during the process, and I had to ctrl+c my way out of it many times (though ctrl+c didn't terminate the whole installer, just the little update popup). Also, I ran the installer script twice and that messed up with some of the apt-get settings. I suggest that after installation is complete, you restore your /etc/apt/sources.list to it's original state, and remove the bleeding edge repositories (unless you know what you're doing). To know what your repository should look like, take a look here.Anyways, one way or the other, your unmet dependencies will be resolved, and then you can use Flexion.
PS: For those trying to use apt-get to install the missing stuff - some of the dependencies aren't available in the default Kali repos, so you'll have to let the script do the installation for you, or manually add the repos to /etc/apt/sources.list (look at the script to find out which repos you need to add)
Dependencies (for newer version)
The only difference lies in the directory structure and name of script. The install.sh script is in the fluxion/install/ directory and not fluxion/ (and is called install.sh instead of Installer.sh) . Basically you just have to change one line. Run the below command on terminal and wait for it to finish executing. Then proceed.
sudo ./install/install.sh
Fluxion
Once again, type the following:
sudo ./fluxion
This time it should run just fine, and you would be asked a few very simple questions.
- For the wireless adapter, choose whichever one you want to monitor on. For the channels question, choose all, unless you have a specific channel in mind, which you know has the target AP.
- Then you will see an airodump-ng window (named Wifi Monitor). Let it run while it looks for APs and clients. Once you think you have what you need, use the close button to stop the monitoring.
- You'll then be prompted to select target.
- Then you'll be prompted to select attack.
- Then you'll be prompted to provide handshake.
- If you don't have a handshake captured already, the script will help you capture one. It will send deauth packets to achieve that.
- After that, I quit the procedure (I was using the script in my college hostel and didn't want to cause any troubles to other students).
 |
| Fluxion using airodump-ng |
If you are with me so far, then you can either just close this website, and try to use the tool on your own (it look intuitive enough to me), or you can read through the test run that I'm going to be doing now.
Getting my wireless network's password by fooling my smartphone into connecting to a fake AP
So, in this example run, I will try to find out the password of my wireless network by making my smartphone connect to a fake AP, and then type out the password in the smartphone, and then see if my Fluxion instance on my Kali machine (laptop) gets the password. Also, for the handshake, I will de-authenticate the same smartphone.
PS: You can probably follow this guide without having any clue how WPA works, what handshake is, what is actually going on, etc., but I suggest you do read up about these things. Here are a few links to other tutorials on this website itself that would prove useful (the first two are theoretical, yet nice, the third one is a pretty fun attack, which I suggest you try out, now or later):
- Things you should know about Wireless Hacking - Beginner Level Stuff
- Things you should know about Wireless Hacking Part II - Intermediate Level Stuff
- Evil Twin Attack
This is the theoretical stuff. Experience with tools like aircrack-ng, etc. would also be useful. Take a look at the navigation bar at the top and look at the various tutorials under the "Wireless Hacking" category.
Anyways, with the recommended reading material covered, you can comfortably move on to the actual hacking now:
The real stuff begins!
This section is going to be a set of pictures with captions below them explaining stuff. It should be easy to follow I hope.
 |
| Select language |
 |
| The scanning process starts, using airodump-ng. |
 |
| You get to choose a target. I'm going after network number 21, the one my smartphone is connected to. |
 |
| You choose an attack. I am going to choose the Hostapd (first one) attack. |
 |
| If you had already captured a 4-way handshake, then you can specify the location to that handshake and the script will use it. Otherwise, it will capture a handshake in the next step for you. (A tutorial on capturing the handshake separately) |
 |
| If you didn't capture a handshake beforehand, then you get to choose which tool to use to do that. I'm go with aircrack-ng. |
 |
| This offers a variety of login pages that you can use to get (phish) the WPA network's password. I went with the first choice. |
 |
| Aircrack-ng tried the password again the handshake, and as expected, it worked. We successfully obtained the password to a WPA-2 protected network in a matter of minutes. |
Video Demonstration
PS: The creator of the video has forked the Fluxion repository, and in the video he cloned from it instead. You may choose to fork from either of those. The original repository being more updated, and forked one being more stable (but less frequently updated). As of the time of creation of the video, both the repositories were the same, so it doesn't make a different which one you clone, but this may not always be the case. In case of any issues, you can probably try cloning both and see which one works for you.
Troubleshooting
Since fluxion and Kali both are constantly evolving (you might be using a different rolling release of Kali, as well as a different version of Fluxion. There are times when the tool break, and there's an interval of time for which it stays broken. Look at the issues page, and you will most probably find a fix for your problem. Note that the issue may as well be in closed issues (it would most probably be in closed issue).
For those who are able to follow the guide to the second last step, but don't get any Login page on their device, this issue suggests a solution. [Dated : 17th September 2016, if you're reading this much later then this might not be relevant, and some other issue would be]
Update : There are some important things mentioned in the README.file on the github repository. See if that helps.
https://github.com/deltaxflux/fluxion/blob/master/README.md
Update : There are some important things mentioned in the README.file on the github repository. See if that helps.
https://github.com/deltaxflux/fluxion/blob/master/README.md
As of 1st November, 2016 (again, might not be relevant if you read this much later), the README suggested this for the no fake login page problem (which seems quite common)-
FakeSites don't workAgain, as I said, it all breaks down to one of two things-
There might be a problem with lighttpd. The experimental version is tested on lighttpd 1.439-1. There are some problems with newer versions of lighttpd. If you problems use the stable version. Check the fix out.
- You are doing some step wrong (easy to fix, follow the tutorial again).
- There is a dependency issue somewhere (some tool has it's wrong version installed). This can be a pain to fix, and there's no guidance I can provide for it really. You'll have to filter through all the issues on the github page of the tool. Hopefully, as the tool grows popular, it'll get more full time developers, and then get integrated in the Kali repository, till then, these problems will continue.
What now?
I illustrated one possible scenario. This script can work with other devices (laptops for example) too as the fooled clients (not just smartphones). One possible short-coming to this attack is that most smartphones/laptops these days don't automatically connect to open networks (unless they have before), and hence the user has to do it manually. If your fake AP has more signal strength than the real one, then a person who doesn't know about WPA and open networks could very easily end up connecting to your network instead. So, overall this attack has a fair chance of succeeding.
Have any problems/comments/suggestions, leave them in the comments below.













It's "sudo ./Installer.sh"
ReplyDeleteUpdated, thanks.
Deletei cannot install Dhcpd and php-cgi
DeleteRead up on what sources.list is, and find out if yours has the required repositories.
DeleteI believe these 3 repos-
deb http://http.kali.org/kali kali-rolling main contrib non-free
deb http://repo.kali.org/kali kali-bleeding-edge main
deb http://ftp.de.debian.org/debian/ jessie main contrib
Should enable you to install the dependencies via apt-get
Yes Ayush Patidar....you are right and tahnx frend for this blog ...& special thanx to fluxion maker...love you.
DeleteNow it's "sudo ./fluxion.sh"
DeleteHello world
DeleteWe Only Make - The boss
Reseller :- Hacking Tools & Hacking services, Also Teach Hacking Methods Via teem weaver or Anydesk,
Each Method Take minimum 1 hour to learn with vedio Tutorial And Hacking Tools ,
How to Make Money With Method & luck ,
- Spamming & Tools ,
- Carding & Tools ,
- Virus with control panal and Spy bot files,
- Virus With Builder And Crypter ,
- Scanners with Bruters ,
- Crypters with Doc Exploits ,pdf Exploits ,TExtfile Exploits ,
- PHP Exploits with shell and mailer
- OTP verications Bypass with Bulletproof Scam-page and Otp control
- Company Ceo or cfo leads Any country
- Rat virus with builder
- Cookies Stealers and Builder
- keyloger and builder
- Credit card Scam-pages
- Bank login Scam-pages
- debit card topup scam page
- donation scam-page
- dhl login and tracking scam-page
- fedax login and tracking scam-page
- Shipping Tools
Place & Ground
learners you will pay cheap $ for demo Tools & Method
Business grounds
Credit card Low Interest Services,
- Credit card with Fullz Information - Minimum Investment 150$ - With 50k Credit limit And balance
- Debit Card Topup AS per Card limit - Minimum Investment 200$ - With 8000$ balance
- Dating scam Fresh male female Logins - Minimum Investment 80$ - Dating Login upto 30
- Tex refund Scam leads - Minimum Investment 200$ - Result upto 5000 in 10 days
- payments and Bills - Minimum Investment 300$ - upto 7000$
- Wester union Minimum Transfer 2000$ - Transfer Fess 400$
-----------------
ABOUT US :
Icq :-675452902
Skype: rushr00t000
email me:- hackitbackd00r@gmail.com
Selling good and fresh cvv fullz
Deletetrack 1 and 2 with pin
bank login
bank transfer
writing cheques
transfer to cc ...
Sell Fresh CVV - Western Union Transfer - Bank Login - Card Dumps - Paypal - Ship
Fresh Cards, Selling Dumps, Cvvs, Fullz
Tickets,Hotels,Credit card topup...Paypal transfer, Mailer,Smtp,western union login,
Book Flight Online
SELL CVV GOOD And HACK BIG CVV GOOD Credit Card
Fresh Cards. Selling Dumps, Cvvs, Fullz.Tickets,Hotels,Credit cards
Sell Cvv(cc) - Wu Transfer - Card Dumps - Bank login/paypal
And many more other hacking services
contact me : hackerw169@gmail.com
ICQ: 699 396 818
- I have account paypal with good balance
- I hope u good customers and will be long-term cooperation
Prices Western Union Online Transfer
-Transfer(Eu,Uk,Asia,Canada,Us,France,Germany,Italy and very
easy to do African)
- 200$ = 1500$ (MTCN and sender name + country sender)
- 350$ = 4000$ (MTCN and sender name + country sender)
- 500$ = 6000$ (MTCN and sender name + country sender)
- 600$ = 8000$ (MTCN and sender name + country sender)
Then i will do transfer's for you, After about 30 mins you'll have
MTCN and sender name + country sender
- Dumps prices
- Tracks 1&2 US = 85$ per 1
- Tracks 1&2 UK = 100$ per 1
- Tracks 1&2 CA / AU = 110$ per 1
- Tracks 1&2 EU = 120$ per 1
Bank Logins Prices US UK CA AU EU
- Bank Us : ( HALIFAX,BOA,CHASE,Wells Fargo...)
. Balance 5000$ = 250$
. Balance 8000$ = 400$
. Balance 12000$ = 600$
. Balance 15000$ = 800$
. Balance 20000$ = 1000$
- Bank UK : ( LLOYDS TSB,BARCLAYS,Standard Chartered,HSBC...)
. Balance 5000 GBP = 300 GBP
. Balance 12000 GBP = 600 GBP
. Balance 16000 GBP = 700 GBP
. Balance 20000 GBP = 1000 GBP
. Balance 30000 GBP = 1200 GBP
contact me : hackerw169@gmail.com
ICQ: 699 396 818
I got my already programmed and blanked ATM card to withdraw the maximum of $1,000 daily for a maximum of 20 days. I am so happy about this because i got mine last week and I have used it to get $20,000. Mike Fisher Hackers is giving out the card just to help the poor and needy though it is illegal but it is something nice and he is not like other scam pretending to have the blank ATM cards. And no one gets caught when using the card. get yours from Mike Fisher Hackers today! *email cyberhackingcompany@gmail.com
DeleteIts an exact copy of linset only difference it's in english and offers many attack languages
ReplyDeleteI haven't used Linset yet, so I don't really know how similar the two tools are (though I know fluxion is built on top of Linset). Anyways, I'll update the post a bit to reflect your point.
Deletegsettings-desktop-schemas : Breaks: mutter (<3.19.92) but 3.18.2-1 is to be in stalled
ReplyDeleteE: Error, pkgProblemResolver::Resolve generated breaks, this may be caused by he ld packpages.
Ignore it, is a sourcelist problem..
DeleteWow, romanian language, I am impressed. Thx for tutorial, I will use for tests :D
ReplyDeleteNo Chance against users with basic technical knowledge, but this spoofing attack maybe much faster then usual wifi cracking methods. It's worth a try
ReplyDeleteBasic technical knowledge is a relative term, you never know how many people might fall for something as simple as this.
DeleteNevertheless, you're right in saying that it doesn't take a lot of thinking for the client to figure out that something's fishy.
I used the VM player with a external wireless card.However the program says there is no wireless cards. I have not solved it.
ReplyDeleteMaybe the external card is connected to the host, not to the virtual machine. I use Kali as my primary OS now so don't exactly remember where the option of switching the wireless card to the guest instead of the host was. Take a look at this pic, it should help.
Deletehttp://geek-university.com/wp-content/images/vmware-player/connect_usb_device.jpg
I used the VM player with a external wireless card.However the program says there is no wireless cards. I have not solved it.
ReplyDeletehey it is possible to change these templates into your own idea?
ReplyDeleteYes.
DeleteYou can navigate to the Sites folder inside Fluxion, and edit any of the templates and change how you want them to look. You can also create new folders there and add them to the script.
i apply all the procedures and every thing goes OK
ReplyDeleteuntil last step
in my smart phone i connected to the fake AP but didn't ask me to login or to insert the password
two last pictures didn't appear
what is the wrong
i will very thankful for replaying me ^^
Are you sure you connected to the fake AP and not the real one? Also, what OS is your smartphone running (for eg. Android)?
Deleteyes I'm sure that i connected to the fake AP and my OS is android 4.3 jelly bean
ReplyDeletei know it's an old version, but is this effect ??
Android 4.3 is fine. I just asked to see if you're using a really uncommon OS or something.
ReplyDeleteIn my case I got a notification right away, clicking which opened the browser window which I posted in the tutorial. Try choosing a different login page (I chose 1, you may try others, see if they work). Try using another smartphone device and see if it works on it.
I too dont get the prompt asking for the passphrase. I checked using one plus two with android - 6 and macbook pro with yosemite
ReplyDeleteI get a notification that the wifi connection you are connected to is not connected to internet, do you want to stay connected or not
DeleteThat can be solved by giving internet access to the fake AP. For that your Kali machine should be connected to the internet. This requires two wireless cards, since the card you are using for creating fake AP can't be used to connect you to the internet simultaneously. If you don't have two cards, try some other way of getting internet access to your Kali machine (eg. USB tethering via smartphone, etc.) and carry out the attack on some other device (not the smartphone used for tethering). See if that works.
DeleteI am running Kali on Parallels desktop and it gets internet access from a virtual lan eth0 port which shares internet to which is my macbook connected. can you guide me how to assign this internet to the fake AP?
ReplyDeleteI think the tool should do that automatically for you. The FakeDNS terminal should do just that. However, you can manually bridge the connections too. Take a look here for something similar. I think that would be helpful.
Deletehttp://www.kalitutorials.net/2014/07/evil-twin-tutorial.html
I had the same problem with him, when I connected to the fake AP, I didn't see any fake login page or any notification
ReplyDeleteAre you sure you followed all the steps properly? I'm not familiar with the implementation details of the tool, so I can't really help if it's a problem with the script.
DeleteIf you can properly describe the problem, it would be useful to open an issue on Fluxion's github. I am not able to re-create the problem myself, and Fluxion seems to work fine for me.
https://github.com/deltaxflux/fluxion/issues
No internet connection issue as encounter by others. Running on Kali linux using VMware. Follow the steps and successfully created fake AP and jammed real AP. When connected to the fake AP, my smartphone (android 6.0.1) notified me there is no internet on the fake AP. I have LAN cable and usb wifi adapter connected. Both can connect to internet but since im using the usb wifi for Fluxion so i connected the system to use LAN cable. I can browser the internet when running Fluxion, so i am not sure what happen in between as well.
ReplyDeleteNo Fake Login Page due to no internet connection.
Deletehttps://github.com/deltaxflux/fluxion/issues/119
Hi
ReplyDeleteI seem to have a different issue. When I get to the option to select an interface, my wireless card shows as option 1, but when I type 1 and press enter it just freezes and nothing happens.
I am running Kali Linux on Virtual box and using an external WLAN card. The WLAN card is picked up in Linux and I can use it to search for other network.
Is this an issue with the script. It seems to freeze Everything on the VM.
Any help would be appreciated.
Thanks
See if the problem is with incompatible versions of Kali and Fluxion. Update kali to most recent, and Fluxion to it's latest stable release.
DeleteWell I used KAli Linux and Fluxion using Virtualbox and at froze exactly as you said. I reinstalled kali linux some three times in Virtualbox and it froze everytime. Then I shifted to Parallels and it worked fine - fine that it jammed real AP and created a fake one but could not get beyond that. My mobile or laptop when connected to the Fake AP did not ever ask for the password
Deletei also got kinda same problem it says wireless card not supported help???
Deletei coudnt get the 4 ways handshake??? please help??
ReplyDeletei could not get the 4 ways handshake ??? please help?
ReplyDeleteCapture it separately and specify the file when Fluxion asks for it. Take a look here-
Deletehttp://www.kalitutorials.net/2014/06/hack-wpa-2-psk-capturing-handshake.html
Could've just mentioned this as evil twin in the title and saved people a click.
ReplyDeleteSorry that you found the title misleading, but there's only so much I can put in there, and I already have en evil twin tutorial and didn't want to cause confusion (Evil Twin)
DeleteHello, I'm having the issue about NO fake login page, checked issue database and says to use backup version, but I can't find it, can you please explain how to use it?.
ReplyDeleteThanks.
wc: /tmp/TMPflux/dump-01.csv: No such file or directory
ReplyDelete./fluxion: line 1280: [: -le: unary operator expected
cat: /tmp/TMPflux/dump-01.csv: No such file or directory
expr: syntax error
WIFI LIST
ID MAC CHAN SECU PWR ESSID
grep: invalid: No such file or directory
grep: number: No such file or directory
grep: of: No such file or directory
grep: lines:: No such file or directory
grep: ‘/tmp/TMPflux/dump-01.csv’: No such file or directory
1) head: invalid number of lines: ‘/tmp/TMPflux/dump-01.csv’ 100%
Problem at the script !
It's work to me thank u Shashwat Chaudhary #<3
ReplyDeleteHappy to be of help, and glad to know it worked without any issues.
Deletehelp me guys i just finished sudo ./Installer.sh command and then i was promoted to white application that says updating system ......and then says installing isc-dhcp-server at that moment it promted me to restart system on finishing package or something like that ........after that i felt like VMware was freezing so finally i restarted it .............so is there any command to begin installing through isc-dhcp-server instead of doing all those steps
ReplyDeleteI don't think restart should be required. If you want to install manually, you can add the required repositories into sources.list, and then use apt-get.
Deleteooh that means by adding those uninstalled list namea in source.list file i must use apt-get command to install those
ReplyDeleteTake a look here-
Deletehttps://github.com/deltaxflux/fluxion/blob/master/add.py
Adding these to your sources.list should be sufficient-
deb http://http.kali.org/kali kali-rolling main contrib non-free
deb http://repo.kali.org/kali kali-bleeding-edge main
deb http://ftp.de.debian.org/debian/ jessie main contrib
Hi, I've made a video tutorial on Fluxion, check it out! Hope you find it useful!
ReplyDeletehttps://www.youtube.com/watch?v=k_X375omYtM
Here is just a thought, and I would love to hear back about the validity of my idea.
ReplyDeleteIs it possible to overload an AP until it stops broadcasting?
If so, then my idea is to implement such a step after all clients have been kicked off, and before our fake network is made available. Our network should be a secure connection with a randomly generated password. But as the system hasn't connected to this network before, The user will be prompted to input the password again. As it should look basically identical to the real, the target user shouldn't hesitate to give us the password.
The second question is that can the password input into the system's network manager and sent over to try to connect with our fake network be logged properly?
1) I don't know enough about how wireless routers behaves when overloaded, so I can't answer that question (whether or not it will stop broadcasting).
Delete2) You create a WPA-2 network with a randomly generated password. The only thing that happens in that case is that the client will try to connect to your network and fail, since the passwords don't match. Now one may think that since he typed the correct password while trying to authenticate into the fake network, the password itself would be sent over to you for validation. However, that's not true. No step of the WPA handshake involves sending plaintext key. The data the client will send you will basically be one step of a handshake (remember, you already have captured a 4-way handshake). The client will wait for your response, validate it, and only then it will participate further in the handshake. Note that since you don't know the password, the client won't even complete the handshake.
Reading what I wrote above, I realize that my explanation is a bit too technical and I should make it easier to understand. So, in basic terms-
1) Client will never send you or anyone the actual password (not even the Real AP).
2) In WPA, the AP verifies that the client knows the correct password, and the client verifies that the AP knows the correct password. So, if you don't know the password, you can't make the AP connect to you. (This is why our fake AP is open)
PS: I've used WPA and WPA2 interchangeably, assume I mean WPA2 everywhere.
DeleteYeah I spent some time researching wireless authentication protocols after I posted my original comment, and realised the passphrase is not exchanged in any way. Thanks though
DeleteBut to kill the real AP would be more access.
ReplyDeleteTo combine WiFi kill with this method would be good
If we can indeed kill the AP, then yes, it would be helpful since our AP would be the only one remaining, increasing the chances of the client connecting.
DeleteRunning Android 6.0.1 on my mobile. Everything goes smoothly for the most part, except for two things: First, updated versions of Chrome seem impervious to this since it just serves up a bad DNS page instead of the fake page from fluxion. Using Samsung's built-in internet client seems to work fine, though, but submitting a password does nothing. The fake page just reloads as if nothing was entered, and no password appears to the right of the client's name as shown in the tutorial video.
ReplyDeleteI'll see if I can recreate these two scenarios, and if I'm able to, I might be able to suggest workarounds.
Deletei,m using kali lite 32 and don,t have fluxion.plus the github command is also not recognized.
ReplyDeleteFirst go this-
Deleteapt-get install git
Then go on with the tutorial.
ok.fine until the airodump scanning and a wifi monitor shows the available wifis.but my fluxion does not ask me any further option and the cursor is stable on a blank screen
Deletefinally mission accomplished man.it,s like try try again.kudos
DeleteGlad to see some comment where a person could get it working even after encountering many difficulties.
DeleteI can not install the bully
ReplyDelete@indra tampo
Deletesearch for a new bully on github and run in a new terminal:
git clone REPLACE_THIS_WITH_THE_NEW_LINK_FROM_GITHUB
and then you must open the folder "bully" (its in the folder "home")
and in the folder bully you see a text document with the name README.xx open it and follow the instruchtions for installing bully.
if you dont can find the README.xx try to run in a new terminal:
cd bully
cd src
sudo make
sudo make install
i hope you can install bully with my instructions!
PS:
DeleteThere is the link:
https://github.com/aanarchyy/bully
and the full command:
git clone https://github.com/aanarchyy/bully
gresit daca hack fluxion nu mai merge ruter cum il vede smartfonul daca acesta este oprit de fluxion
ReplyDeleteHello
ReplyDeleteI used the terminal commands.
Everything went ok..
But when i type sudo ./Installer.sh
The 4 dependencies stay stuck on installing..and never finish installing...then i tried sudo ./fluxion and it says they are not installed
have u updated the repositories...
DeleteI cannot see the same SSID at my phone and mac, can you give me a answer? does the mac or phone auto. filter it?
ReplyDeletei updated repo many times ...even though it is showing error message as unable to locate package Hostapd...but successfully installed all other packages..pls help me.
ReplyDeleteTry to manually install hostapd using apt-get.
DeleteYour sources.list file should have the proper repositories. After fixing the repositories you need to perform apt-get update.
This is the repo which should always be there (for Kali Rolling)
deb http://http.kali.org/kali kali-rolling main contrib non-free
This repo may be required at some times, but should be removed after use-
deb http://repo.kali.org/kali kali-bleeding-edge main
Once repos are added, apt-get update done, just run this-
apt-get --yes install hostapd
cool I like it very much.Can we show mikrotik hotspot login page instead wpa password page to the victim.Here I am giving you an image of mikrotik hotspot login page if u dont know.
ReplyDeleteClick here to see image
Hope u understand my question.
I want to know can we do it?If yes then plz tell me how?
Waiting for ur reply.
The installer script won't install all the dependencies, or may not have installed any missing dependencies. Here's what I get -
ReplyDeleteAircrack-ng.....OK!
Aireplay-ng.....OK!
Airmon-ng.......OK!
Airodump-ng.....OK!
Awk.............OK!
Bully...........OK!
Curl............OK!
Dhcpd...........Not installed (isc-dhcp-server)
Hostapd.........Not installed
Iwconfig........OK!
Lighttpd........Not installed
Macchanger......OK!
Mdk3............OK!
Nmap............OK!
php-cgi.........Not installed
Pyrit...........OK!
Python..........OK!
Reaver..........OK!
Unzip...........OK!
Xterm...........OK!
Zenity..........OK!
Openssl.........OK!
rfkill..........OK!
strings.........OK!
fuser...........OK!
What do I do now? I'm new to all this and Kali Linux, but I've been using Linux Mint and Ubuntu for several years. I don't think I should have typed sudo while already root, so I tried to install without sudo, but it made no difference.
sudo is not needed, I use it because I use kali as a regular user (it's my primary OS), and an extra sudo doesn't change anything for the root users so adding it makes no difference.
DeleteIf you're familiar with Linux, then try the following fix-
1) Find out the repos where these tools are.
2) Add them to your sources.list
3) Install the tools manually
These fluxion source files might help-
Simple and short python script which adds required repos to your sources.list
https://github.com/deltaxflux/fluxion/blob/master/add.py
Longer but still simple python script which installs the dependencies (to look for something, do ctrl+f and search for lighttpd and so on, and look at the commands)
https://github.com/deltaxflux/fluxion/blob/master/Installer.sh
when i use airodump-ng, i can see my hidden wifi immediately, but when I use fluxion can't see my hidden wifi, even when I tried to force scan with one channel only.
ReplyDeleteWhat could be my problem is?
if no handshake is being captured, then how to proceed ?? any suggestion
ReplyDeleteworks fine but one problem bro.
ReplyDeleteActually my ssid is combination of words and some emos..
It created a fake ap with text, replacing emos with combination of words and letters, so no one has connected to that fake one and no out come ;)
Having issue...it says Corrupted when running the see handshake part, any help?
ReplyDeleteI am having the same problem.
DeleteWell, i have a WIFI usb card, Airmon shows it, But fluxion wont work with it: Does Anywone know a solution??
ReplyDeleteNo one is automatically connecting to fake AP like |wifiphisher| they need to manually connect the FAke Ap then only they can view Fake Page on browser no on APP
ReplyDeleteHey, i have a sligt problem... "
ReplyDelete[~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~]
[ ]
[ FLUXION 0.24 < Fluxion Is The Future > ]
[ ]
[~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~]
[i] Select your language
[1] English
[2] German
[3] Romanian
[4] Turkish
[5] Spanish
[6] Chinese
[7] Italian
[8] Czech
[9] Greek
[10] French
[deltaxflux@fluxion]-[~]^[[D^[[A^[[C^[[B^[[D^[[A^[[C^[
those signs are my arrow keys..
and thats only after i started Fluxion.
my arrows work fine on just terminal..
Thanks
hi guys, please help
ReplyDeletei am finished capturing handshake. but after that, no fake AP has been detected nor created using my internal card.
using my usb wifi, i cant even establish handshake capturing. Once i selected a network. ALl client in that network disconnect but cannot connected until attack has being cancel. so while attacking, cannot connect to the target network.
please advise. most of my allowance goes to data subscription. please help
please help
make sure your card support monitor mode. Im using usb wireless Alfa AWUS036H
ReplyDeletei have a problem.after installing fluxion it doesn't ask to choose language or anything .just red color big fluxion logo.latest rev. [137]
ReplyDeleteHii what is the username and password when you try to install git clone https://github.com/wi-fi-analyzer/fluxion?
ReplyDeleteIt shouldn't be asking for a password. Please upload and link screenshot so I can find out what's causing this.
Deleteloginin in github for username and password or browser in other urll
DeleteHey mate i have a problem here. Im tryin to acquire my networks password by it and i make all the steps but when i get to the final step where it tries to deauth with mkd3 everyone so they connect ot the fakeAP it stucks there and it does nothing. It doesnt even start deauth. What would be the problem?
ReplyDeletei am not getting wifi router list on the fluxion terminal
ReplyDeleteFile: fluxion-master.zip
ReplyDeleteReview: 136
Version: 0.25
Date: 27/02/2017
MD5: 7f000a0ae2d9d0f7a6a0218917a7c9f1
Download:
https://www.sendspace.com/file/cw5ge0
http://www105.zippyshare.com/v/KgdtS3bo/file.html
http://s000.tinyupload.com/?file_id=20814710211043351016
taking time to download fluxion
ReplyDeletewhat to do ??
more than half hour
works on my old hp laptop but it shows an error on my new acer laptop.any fix??
ReplyDeleteerror :
wc: /tmp/TMPflux/dump-01.csv: No such file or directory
./fluxion: line 1280: [: -le: unary operator expected
cat: /tmp/TMPflux/dump-01.csv: No such file or directory
expr: syntax error
WIFI LIST
ID MAC CHAN SECU PWR ESSID
grep: invalid: No such file or directory
grep: number: No such file or directory
grep: of: No such file or directory
grep: lines:: No such file or directory
grep: ‘/tmp/TMPflux/dump-01.csv’: No such file or directory
1) head: invalid number of lines: ‘/tmp/TMPflux/dump-01.csv’ 100%
hey all .. my issue , hidden network get lots of data but no wpa handshake i can get the hidden networks name @ times .
ReplyDeleteany suggestions
error :
ReplyDeletewc: /tmp/TMPflux/dump-01.csv: No such file or directory
./fluxion: line 1280: [: -le: unary operator expected
cat: /tmp/TMPflux/dump-01.csv: No such file or directory
expr: syntax error
WIFI LIST
ID MAC CHAN SECU PWR ESSID
grep: invalid: No such file or directory
grep: number: No such file or directory
grep: of: No such file or directory
grep: lines:: No such file or directory
grep: ‘/tmp/TMPflux/dump-01.csv’: No such file or directory
1) head: invalid number of lines: ‘/tmp/TMPflux/dump-01.csv’ 100%
Hello,
ReplyDeleteI've been using fluxion for a while,
I would like to know is it possible to use sslstrip with fluxion ? as I wanna downgrade victim's https request to http :)
Waiting for your reply eagerly,
Thanks
It says after I do sudo ./fluxion this
ReplyDelete"wc: /tmp/TMPflux/dump-01.csv: no such file or directory"
"./fluxion:line 1218: [: -le: unwary operator expected"
"cat: /tmp/TMPflux/dump-01.csv: no such file or directory"
"expr: syntax error"
Then where the wifi list is it says
"grep: invalid: no such file or directory"
"grep: number: no such file or directory"
"grep: of: no such file or directory"
"grep: lines:: no such file or directory"
"grep: '/tmp/TMPflux/dump-01.csv': no such file or directory"
Yes I would love a solution to this issue as well.
DeleteHello!
ReplyDeleteSo, when I tell it to scan all channels for wifi networks, it finds nothing. Of course, when I do it manually with airodump-ng I find all sorts of networks. I am not sure why this is happening.
Hostapt method does nothing after started
ReplyDeleteI am trying to hack wifi password in kali linux by fluxion. But in the stage of captuing handshake. i found our target network hand shake but it shows corrupted.
ReplyDeletewhat it`s solution?
no one answer now, when I tell it to scan all channels for wifi networks, it finds nothing. And on the terminal an error appear that tell me error with the network manager protocols are not supported
ReplyDeletehow to install sites in fluxion
ReplyDeleteSir, I had a question can I use websploit in another terminal to jam victims genuine AP. And force victim to click on our fake Ap. Is that possible?
ReplyDeleteSudo ./fluxion.sh
ReplyDeleteAny help? So I captured the handshake but then I get the following:
ReplyDeleteCertificate invalid or not present, please choice
[1] Create a SSL certificate
[2] Search for SSl certificate
[3] Exit
Choose 1
DeleteVery very nice site. Amazing and detailed posts. Keep up good work.
ReplyDeleteWindows 9 Ultimate 2015
I'm pretty sure it's not a big deal but it's driving me insane whenever I use the ./fluxion or ./installer.sh it doesnt work
ReplyDeleteAll I got is : "commande introuvable" (means that command line doesn't exist..)
Any help, please ?
Thank's..
Any suggestions on this error " Certificate invalid or not present, please choice
ReplyDeleteThank you if you can help
bhai aapke article copy kiye jaa rahe ( https://null-byte.wonderhowto.com/forum/wifi-hacking-crack-wep-wpa-wpa2-password-without-dictionary-bruteforce-new-methode-fluxion-0174280/ ) btao hadd he, aapne hi iss site ko top 5 best site to learn me mention kiya tha
ReplyDeleteInstead of using ./fluxion
ReplyDeleteuse
./fluxion.sh
This helped me tremendously. Everything went smoothly from then on. Oh and if your having trouble with the fake ap not asking you for password. Go to your browser NOT CHROME and type an unsecured url that doesn't have (https)
I typed www.primewire.com and the fake ap popped up asking for password. Hope this helped.
Sidenote: I really wish the fake ap login page didn't look so suspicious. I think even Stevie Wonder could tell it was a hack. lol
KRACK Attacks: Breaking WPA2
ReplyDeleteHello man ! I hope you're still active on this article.
ReplyDeleteI got Fluxion to work, until the very last step : Client connect to my AP, but no fake request is prompted. So i tried to give the Fluxion AP internet acces via the brctl commands you gave in you EvilTwin article (bridging FXan0AP to usb0, my phone tethering).
Then again, it looked like the Fluxion AP crashed. AP Jammer telling me "read() failed: network is down" and the AP windows : "DHCP request [...] : wrong network"
Thoughts on it ?
I never gave fluxion internet access and it all working 100% from this guide. On running it once completed did u connect to the fake AP open clone with a second test computer or phone? On joining the fake Ap i then open a webpage and the fake log in page opens for me asking to enter password. sorry i cant help to much but hope that helps.
DeleteHi guys, can anyone help me by how to open fluxion on nethunter, it always gives me the "x (graphical) thing
ReplyDeleteHi guys, can anyone help me by how to open fluxion on nethunter, it always gives me the "x (graphical) thing
ReplyDeleteI think it should be "sudo ./fluxion.sh"
ReplyDeleteHEY IS THIS FULLY LEGIT I MEAN DOES IT WORK BCUZ IF IT DOES THEN YOU ARE SERIOUSLY THE GREATEST PERSON I'VE EVER KNOWN!!!!!!
ReplyDelete404 Not Found
ReplyDeleteE: Failed to fetch http://http.kali.org/kali/pool/main/b/bind9/libisccc-export140_9.10.3.dfsg.P4-12.6_amd64.deb 404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/b/bind9/libisccfg-export140_9.10.3.dfsg.P4-12.6_amd64.deb 404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/b/bind9/libirs-export141_9.10.3.dfsg.P4-12.6_amd64.deb 404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/i/isc-dhcp/isc-dhcp-server_4.3.5-3_amd64.deb 404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/libs/libselinux/selinux-utils_2.7-1_amd64.deb 404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/p/policycoreutils/policycoreutils_2.6-3_amd64.deb 404 Not Found
E: Unable to fetch some archives, maybe run apt-get update or try with --fix-missing?
hello , i have everything working fine. iso , imac , ipad , laptop"windows" all connect fine with internet. but andriod devices connect but get the no internet. any ideas what stopping andriod devices working propler the 2 i tried was google pixel and blackberry priv
ReplyDeletefluxion linset airset deveriam ter atualização principalmente para que as páginas https fossem redirecionada também.
ReplyDelete
ReplyDeleteBEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE..... Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . .......... EXPLANATION OF HOW THESE CARD WORKS.......... You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $5,000, 2nd VAULT $10,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly... Done. ***NOTE: DON'T EVER MAKE THE MISTAKE OF CLICKING THE "ALL" OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com). We are located in USA.
Yeah. I have hacked with KALI -- Linux. but without it, can be a nice experience. :D
ReplyDeleteLED LCD TV Repairing Course in Delhi
LED LCD Smart TV Repairing Course in Delhi
LED Smart TV Repairing Course in Delhi
Mobile Repairing Institute in Delhi
Mobile Repairing Course in Laxmi Nagar
Mobile Repairing Institute in Laxmi Nagar
LED LCD TV Repairing Institute in Delhi
Computer Hardware Repairing Course in Delhi
Mobile Repairing Course in Delhi
I have used this method. Great tutorial. Nice share. :) Appreciated (y)
ReplyDeletemobile repairing course in delhi
mobile repairing institute in delhi
mobile repairing institute in laxmi nagar
led lcd smart tv repairing course in delhi
led lcd tv repairing course in delhi
led lcd tv repairing course in laxmi nagar
cctv repairing course in delhi
cctv repairing institute in delhi
laptop repairing course in delhi
laptop repairing institute in delhi
AC repairing course in delhi
AC repairing institute in delhi
"mdk3 deauth preiodically re-reading blacklist/whitelist every 3 seconds" is not responding please help?
ReplyDeletegood day sir! I would like to congratulate you for this wonderful tutorials you have. May ask if this procedure requires your exploiting machine to be connected to the other source of internet(tether or something) or not? I read from the above thread about some sort of issues about the fake ap and you answered them they must be connected to some other internet source to make it work? does the entire procedure requires it or specific to those who encountered the above issue? thanks and more power to you.
ReplyDeleteI can’t imagine focusing long enough to research; much less write this kind of article. You’ve outdone yourself with this material. This is great content. wlan passwort knacken
ReplyDeleteBEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE..... Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . .......... EXPLANATION OF HOW THESE CARD WORKS.......... You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $1,000, 2nd VAULT $5,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly... Done. ***NOTE: DON'T EVER MAKE THE MISTAKE OF CLICKING THE "ALL" OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com) We are located in USA.
ReplyDeleteA very awesome share you have did .. Keep sharing like this way .. Thank you :)
ReplyDeleteVaastu consultant Vaastu consultant in India
Vaastu consultant in Delhi
Vaastu consultant in Delhi ncr
Vaastu consultant in East Delhi
Vaastu consultant in South Delhi
Vaastu consultant in Noida
Vaastu consultant in Ghaziabad
Vaastu consultant in Gurgaon Guru gram
Vaastu consultant in Faridabad
Vaastu Expert
Vaastu Expert in India
Vaastu Expert in delhiVaastu consultant Vaastu consultant in India
Vaastu consultant in Delhi
Vaastu consultant in Delhi ncr
Vaastu consultant in East Delhi
Vaastu consultant in South Delhi
Vaastu consultant in Noida
Vaastu consultant in Ghaziabad
Vaastu consultant in Gurgaon Guru gram
Vaastu consultant in Faridabad
Vaastu Expert
Vaastu Expert in India
Vaastu Expert in delhi
Hey everyone , I don't really know much about this hacking things but I can direct you to a professional hacking company who helped me to track and hack my boyfriend's iPhone and his Facebook respectively.. If you need to check on your partner's sincerity, employee's honesty, recover your email passwords, Social networks (i.e Facebook, Twitter, IG), change your school grades, clear your criminal records, gain access to bank accounts,spy on phone. you can just contact them at ... Their charges are minimal and negotiable contact them at [cyberhelp027@gmail….com]..tell him you are from me or text them on +16629671749 .... You can thank me later......
ReplyDeleteHello World -
ReplyDeletehoping one of your geniuses could shed some light on a fluxion issue Im having.
ive been reading, watching, testing and researching and ive not been able to find a solution so far.
Im using a full install of Kali Linux 64 bit 2018.4 edition. Installed on a partition drive of an Alienware 15R.
Fluxion edition 0.23 rev 44.
Wifi Interface Ralink Tech ALFA AWUS036h
Im testing my Wifi penetration skills on various routers I own, for the most part im testing on an Apple Airport Express, on which ive already had success with brute force penetration tools. These routers are my own, and are live with an incoming internet connection.
Research has lead me to Fluxion - i did have to manually update some dependancies myself - successfully - fluxion seems to work correctly from what i can tell.
The issue im having is right at the end of all of the tutorials ive seen - handshake sucessfully grabbed, or .cap file loaded. I successfully deauthorised my iphone and or a second laptop (mac air).
Ive successfully created a fake AP, and ive successfully been sent to that AP on my phone (interestingly not on my Mac Air (?) ) Although i have noticed that this stage in the process can be a bit hit and miss sometimes certain fake login pages work, sometimes certain ones dont. Ive not worked out the variables of this yet.
either way - Fake AP accessed by device - password entered, confirm button clicked.
Then nothing.
Aircrack-ng doesnt seem to open automatically like all the tutorials ive seen. I cant find any documents that show me ive missed out a step - the password has definitely been entered correctly as its my wifi network, my password and my device from which its been entered.
can anyone shed any light on this for me?
ReplyDeleteNow days yoga asanas is in more demand most of the people like yoga there are many asanas which are helpful for losse weight but that is possible with some special guidance so for any information regarding yoga pose please click on my link.
Here you will also find best benefits of yoga which will great effect on your body comparatively other exercise with the help of it you can also build a muscle, so here I my article have some selected best yoga pose which help you easily build a muscle.
how to remove pimples,
shoulder exercise,
workout session,
best supplement store in amritsar,
how to get rid of hair fall
Hey everyone , I don't really know much about this hacking things but I can direct you to a professional hacking company who helped me to track and hack my boyfriend's iPhone and his Facebook respectively.. If you need to check on your partner's sincerity, employee's honesty, recover your email passwords, Social networks (i.e Facebook, Twitter, IG), change your school grades, clear your criminal records, gain access to bank accounts,spy on phone. you can just contact them at ... Their charges are minimal and negotiable contact them at [cyberhelp027@gmail….com]..tell him you are from me or text them on 8623077432.... You can thank me later......
ReplyDeleteCan you make a tutorial on atrack using pmkid?
ReplyDeleteI heard it's the new method for wpa/wpa2 attacks.
How could I possibly install 7zr? It says module not found.
ReplyDeletecontact elizabethjone146@gmail.com
ReplyDeletebest hackers it help me to hack my my husband old account hello everybody if you want to hack anything social media like Gmail Facebook Hotmail account Snapchat Yahoo line Instagram WhatsApp account icould password Apple remove icould password Twitter account POS bank account details kik dating site tracking someone dating site cheating man or woman criminal record phone number hack PayPal iMessage account telegram Bitcoin SSN aol Outlook anything social media just contact elizabethjone146@gmail.com or text them on Whatsapp+18573255825 best hacker it help me many people am very surprised am happy just contact them you will happy
contact : elizabethjone146@gmail.com WhatsApp +18573255825 Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
ReplyDeleteDo you need to retrieve your stolen bitcoin?
Do you need to increase your credit score?
Do you intend to upgrade your school grade?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : elizabethjone146@gmail.com WhatsApp +18573255825
contact : elizabethjone146@gmail.com WhatsApp +18573255825 Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
ReplyDeleteDo you need to retrieve your stolen bitcoin?
Do you need to increase your credit score?
Do you intend to upgrade your school grade?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : elizabethjone146@gmail.com WhatsApp +18573255825
elizabethjone146@gmail.com WhatsApp +18573255825
ReplyDeletehello everybody if you Need a good hacker? A senior member of ice fog hackers.A professional in the areas mentioned below:
1. hotmailfacebook,whatsapp,emails,twitter and instagram hack
2- Hacking computer system
3- Cloning of phones
4- Changing DMV records without leaving traces
5- Changing school grades without leaving traces
6- Retrieving hacked social media accounts
7- Credit card hack
8- Clearing criminal records
9- Clearing of bad driving records without leaving traces
10- Website hack
11- Retrieving hacked social media accounts
12- P.I – Private investigator like cheating husbands or wives and any other P.I activities and so many other services.
13- Catch hacker scammers
14- Wire transfer to any bank
15- Retrieval of hacked accounts (facebook,twitter,instagram,zoosk,match etc..)
16- Bank login
17- Phishing emails. to mention a few..He is at your service if you need him.
Contact elizabethjone146@gmail.com WhatsApp +18573255825
is the best of hacker try elizabeth you will happy about your work
Never settle for a cheating spouse. Contact elizabethjone146@gmail.com
ReplyDeleteWhatsApp +18573255825 for any form of hack like
1-DATABASE HACK.
2-WHATSAPP HACK
3-WEBSITE HACK
4-TRACKING CALLS
5-PHONE CLONE
6-FACEBOOK HACK
7-CHANGE SCHOOL GRADE
8-ONLINE RECORDS CHANGES
9-BANK ACCOUNT HACK
10-ERASE CRIMINAL RECORDS
11-ONLINE HACKING LECTURES
12-WORLD PRESS BLOGS HACK
13-CONTROL DEVICES REMOTELY HACK
14-SALES OF DUMPS CARDS & CC OF ALL KIND
15-RETRIVAL OF HACKED SOCIAL MEDIA ACCOUNTS
16-INCREASE CREDIT SCORE
i have used this hacker services more than 5 times and it has always worked try him and thank me later. you Contact elizabethjone146@gmail.com
WhatsApp +18573255825
contact : elizabethjone146@gmail.com WhatsApp +18573255825 Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
ReplyDeleteDo you need to retrieve your stolen bitcoin?
Do you need to increase your credit score?
Do you intend to upgrade your school grade?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : elizabethjone146@gmail.com WhatsApp +18573255825
Hello Everybody,
ReplyDeleteMy name is Mrs Sharon Sim. I live in Singapore and i am a happy woman today? and i told my self that any lender that rescue my family from our poor situation, i will refer any person that is looking for loan to him, he gave me happiness to me and my family, i was in need of a loan of $250,000.00 to start my life all over as i am a single mother with 3 kids I met this honest and GOD fearing man loan lender that help me with a loan of $250,000.00 SG. Dollar, he is a GOD fearing man, if you are in need of loan and you will pay back the loan please contact him tell him that is Mrs Sharon, that refer you to him. contact Dr Purva Pius, call/whats-App Contact Number +918929509036 via email:(urgentloan22@gmail.com) Thank you.
contact : elizabethjone146@gmail.com WhatsApp +18573255825 Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
ReplyDeleteDo you need to retrieve your stolen bitcoin?
Do you need to increase your credit score?
Do you intend to upgrade your school grade?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : elizabethjone146@gmail.com WhatsApp +18573255825
Never settle for a cheating spouse. Contact elizabethjone146@gmail.com
ReplyDeleteWhatsApp +18573255825 for any form of hack like
1-DATABASE HACK.
2-WHATSAPP HACK
3-WEBSITE HACK
4-TRACKING CALLS
5-PHONE CLONE
6-FACEBOOK HACK
7-CHANGE SCHOOL GRADE
8-ONLINE RECORDS CHANGES
9-BANK ACCOUNT HACK
10-ERASE CRIMINAL RECORDS
11-ONLINE HACKING LECTURES
12-WORLD PRESS BLOGS HACK
13-CONTROL DEVICES REMOTELY HACK
14-SALES OF DUMPS CARDS & CC OF ALL KIND
15-RETRIVAL OF HACKED SOCIAL MEDIA ACCOUNTS
16-INCREASE CREDIT SCORE
i have used this hacker services more than 5 times and it has always worked try him and thank me later. Contact elizabethjone146@gmail.com
WhatsApp +18573255825
contact
ReplyDeleteelizabethjone146@gmail.com or text them on Whatsapp +18573255825 Do you suspect your partner of cheating? are you being overly paranoid
or seeing signs of infidelity?Then he sure is cheating: I was in that
exact same position when I was referred through my best friend Monique
who helped me hack into my girlfriend’s phone, it was like a miracle
when he helped me clone my girlfriend phone and I got first-hand information
from his phone. Now I get all his incoming and outgoing text messages, emails, call
logs, web browsing history, photos and videos, instant messengers (facebook,whatsapp,bbm,IG
etc) GPS locations, phone tap to get live transmissions
on all phone conversations.You can also contact
elizabethjone146@gmail.com or text them on Whatsapp +18573255825
best hacker I know a hacker who can help you spy on your cheating boyfriend's / girlfriend's / spouse phone, whatsapp, facebook, or other platforms just contact elizabethjone146@gmail.com
ReplyDeleteWhatsApp +18573255825 he is the best out there, he is a professional, trustworthy hacker, he helped reveal my ex husband secret affairs, he also helped settle bank loans, thanks to him I am now a free woman , contact him and he will leave you happy then you can thank me later
I want to testify about United blank atm cards which can withdraw money from any atm machines around the world. I was very poor before and have no job. I saw so many testimony about how United hackers send them the atm blank card and use it to collect money in any atm machine and become rich. I email them also and they sent me the blank atm card. I have use it to get 90,000 dollars. withdraw the maximum of 5,000 USD daily. United hackers is giving out the card just to help the poor. Hack and take money directly from any atm machine vault with the use of atm programmed card which runs in automatic mode.
ReplyDeleteEmail: unitedblankatmhackcard@gmail.com
Hi
ReplyDeletePlease Fluxion 0.25 download
HELP
Selling good and fresh cvv fullz
ReplyDeletetrack 1 and 2 with pin
bank login
bank transfer
writing cheques
transfer to cc ...
Sell Fresh CVV - Western Union Transfer - Bank Login - Card Dumps - Paypal - Ship
Fresh Cards, Selling Dumps, Cvvs, Fullz
Tickets,Hotels,Credit card topup...Paypal transfer, Mailer,Smtp,western union login,
Book Flight Online
SELL CVV GOOD And HACK BIG CVV GOOD Credit Card
Fresh Cards. Selling Dumps, Cvvs, Fullz.Tickets,Hotels,Credit cards
Sell Cvv(cc) - Wu Transfer - Card Dumps - Bank login/paypal
And many more other hacking services
contact me : hackerw169@gmail.com
ICQ: 699 396 818
- I have account paypal with good balance
- I hope u good customers and will be long-term cooperation
Prices Western Union Online Transfer
-Transfer(Eu,Uk,Asia,Canada,Us,France,Germany,Italy and very
easy to do African)
- 200$ = 1500$ (MTCN and sender name + country sender)
- 350$ = 4000$ (MTCN and sender name + country sender)
- 500$ = 6000$ (MTCN and sender name + country sender)
- 600$ = 8000$ (MTCN and sender name + country sender)
Then i will do transfer's for you, After about 30 mins you'll have
MTCN and sender name + country sender
- Dumps prices
- Tracks 1&2 US = 85$ per 1
- Tracks 1&2 UK = 100$ per 1
- Tracks 1&2 CA / AU = 110$ per 1
- Tracks 1&2 EU = 120$ per 1
Bank Logins Prices US UK CA AU EU
- Bank Us : ( HALIFAX,BOA,CHASE,Wells Fargo...)
. Balance 5000$ = 250$
. Balance 8000$ = 400$
. Balance 12000$ = 600$
. Balance 15000$ = 800$
. Balance 20000$ = 1000$
- Bank UK : ( LLOYDS TSB,BARCLAYS,Standard Chartered,HSBC...)
. Balance 5000 GBP = 300 GBP
. Balance 12000 GBP = 600 GBP
. Balance 16000 GBP = 700 GBP
. Balance 20000 GBP = 1000 GBP
. Balance 30000 GBP = 1200 GBP
contact me : hackerw169@gmail.com
ICQ: 699 396 818
I want free internet please
ReplyDeleteYou guys have surpassed my expectations! James is seriously amazing and is doing everything to help my Fiancé and me, in1weeks my credit score went up 700 points and I can only imagine what is to come. Thank you for the excellent customer service and doing exactly what you all have set out to do! NO GIMMICKS OR BS with you guys.They carry out any kind of hacks You can reachout to them via Hackintechnology@gmail.com +16692252253
ReplyDeleteAre you looking for prove to know if your spouse is cheating on you just mail elizabethjone146@gmail.com
ReplyDeleteWhatsApp +18572012269 his really a God sent to me and i really appreciate his good work that he did for me this hacker broke into my husband phone cause i felt my husband was cheating on me then i contacted elizabethjone146@gmail.com
WhatsApp +18572012269 for help i couldn't believe that this great hacker was able to hack into my husband cell and brought me all his social media messages he uses and all the call logs\text messages\deleted text messages and many more this hacker is good inbox him if you need help in hacking best hacker
contact
elizabethjone146@gmail.com
WhatsApp +18572012269
Garry cole
ReplyDeleteGREETINGS EVERYONE, are you looking for a LEGIT and Trustworthy HACKERS with 100% Guarantee and you want to get your job done urgently withing one Hour or you are face with delay and unnecessary excuses and error on your job?. Then Worry no more because easyhackingguru@gmail.com are the Best Bet in any hacking Services. They are ready to render and attend to your job with swift response and No delay at all.
Their services are outlined as follows:
. LONG TIME LOAN GIVING
. PROFESSIONAL in SCHOOL GRADE changing
. WHATSAPP Hack
. FACBOOK hack
. PROFESSIONAL in any BANK ACCOUNTS TRANSFER
. TWITTERS hack
. EMAIL,YAHOOMAIL and HOTMAIL ACCOUNTS hack
. WEBSITE CRASHED hack
. SERVER CRASHED hack
. SALES OF SPYWARE and KEYLOGGER SOFTWARE
. RETRIVAL OF LOST FILES and DOCUMENTS
. ERASE and EXPUNGE of CRIMINAL RECORDS
. DATABASE hack
. SALES of ATM CARDS in WHITE
. SKYPE hack
. PAYPAL hack
. DROPBOX ACCOUNT hack and Lots more..........
CONTACT: their services at easyhackingguru@gmail.com and you will be glad you did
whatsApp contact- +1(216)525-9704Call/Text - +1(216)525-9704
This blog was how do I say it? Relevant!! Finally I have found something which helped me. Thanks!
ReplyDeleteThey are all scammers, they will make you pay after which they will give you an excuse asking you to pay more money, they have ripped me of $2000, i promised i was going to expose them. I figured it all out when my colleague took me to Pavel (HACKINTECHNOLOGY@GMAIL.COM) +1 669 225 2253 He did perfect job, he hacks all accounts ranging from (Emails, Facebook, whatsapp, imo, skype, instagram, Phone cloning, DMV removal, tracking locations, background checks Kik etc. he also hacks cell phones, cell phone tapping and cloning, clears bad driving and criminal records, bank transfers, locates missing individuals e.t.c. You should contact him and please stop using contacts you see on websites to execute jobs for you, you can ask around to find a real hacker
ReplyDeleteCan you make video how you are doing it? And post it on youtube? I would buy youtube views for you from this site https://viplikes.net/
ReplyDeleteAivivu chuyên cung cấp
ReplyDeletevé máy bay tết 2021
vé máy bay đi Mỹ giá bao nhiêu
ve may bay di Phap
vé máy bay đi hàn quốc vietnam airline
vé máy bay đến nhật
vé máy bay đi anh bao nhiêu tiền
Awesome job! The Acadecraft provides content writing services through a team consisting of Subject Matter Experts specialized in different concept fields, and also disciplines for undergraduate, post-graduate, and Ph.D. levels. Our SMEs have the ability to create content that is mapped to meet the learning objectives of the curriculum.
ReplyDeletecontent development services online
ReplyDeleteThis professional hacker is absolutely reliable and I strongly recommend him for any type of hack you require. I know this because I have hired him severally for various hacks and he has never disappointed me nor any of my friends who have hired him too, he can help you with any of the following hacks:
-Phone hacks (remotely)
-Credit repair
-Bitcoin recovery (any cryptocurrency)
-Make money from home (USA only)
-Social media hacks
-Website hacks
-Erase criminal records (USA & Canada only)
-Grade change
Email: cybergoldenhacker at gmail dot com
If you can create significantly more with an investment and also have an emergency savings fund put aside, you may make a bigger financial impact investing than reducing your mortgage. mortgage calculator canada Life, however, is moving too fast and much more responsibilities are coming your way. mortgage payment calculator canada
ReplyDeleteThanks for the post it easily helped me to understand the important parts.
ReplyDeleteHappy to visit your blog, I am by all accounts forward to more solid articles and I figure we as a whole wish to thank such huge numbers of good articles, blog to impart to us.
ReplyDeletecertification of data science
Aivivu chuyên vé máy bay, tham khảo
ReplyDeletevé máy bay đi Mỹ giá bao nhiêu
vé máy bay từ los angeles về việt nam
vé máy bay vietjet từ nhật về việt nam
vé máy bay khứ hồi từ đức về việt nam
vé máy bay từ hàn quốc về việt nam
Honestly am the luckiest student to get my poor school grades fixed within the space of 1 hour spyexpert0@gmail.com did a wonderful job for me at an affordable price. I really feel so happy telling the world about spyexpert0@gmail.com
ReplyDeletencie
ReplyDeleteI read about jeajamhacker@gmail.com on the internet as one of the best hacker ever and am really glad this hacker was able to do the job most hackers could not do, am forever grateful to jeajamhacker@gmail.com I have come across 2 to 3 hackers but yet they fail me at the end but just my first contact with jeajamhacker@gmail.com I got the best ever with out being traced by my spouse.
ReplyDeleteReally nice and interesting post. I was looking for this kind of information and enjoyed reading this one. Keep posting. Thanks for sharing.
ReplyDeleteBest Data Science courses in Hyderabad
Just because of jealousy my friend decided to snatch my man I found out with the help of a hacker who was able to help me crack my man phone and I read a lot of lies my friend has been telling my man about me on both WhatsApp messages and iMessage thank you russiancyberhackers@gmail.com for unveiling there secrets
ReplyDeleteHe is a professional hacker, he is absolutely reliable and I strongly recommend him for any types of hacking jobs you require. why i said this is because I have engaged him severally in various hacking jobs and he has never disappointed me nor any of my friends who have hired him also, He has really proven himself to be a professional and a reliable hacker, He can help you out with any hacking jobs including this:
ReplyDelete-Cell Phones hacking (remotely)
-Credit Repair
-Bitcoin Recovery (Any type of Cryptocurrencies)
-Make money from Home (Any Countries)
-Social media Hacking
-Website Hacking
-Erasing of criminal Records (Any Countries)
-Grade Change
Email him via: hackingsetting50@gmail.com
He is a professional hacker, he is absolutely reliable and I strongly recommend him for any types of hacking jobs you require. why i said this is because I have engaged him severally in various hacking jobs and he has never disappointed me nor any of my friends who have hired him also, He has really proven himself to be a professional and a reliable hacker, He can help you out with any hacking jobs including this:
ReplyDelete-Cell Phones hacking (remotely)
-Credit Repair
-Bitcoin Recovery (Any type of Cryptocurrencies)
-Make money from Home (Any Countries)
-Social media Hacking
-Website Hacking
-Erasing of criminal Records (Any Countries)
-Grade Change
Email him via: hackingsetting50@gmail.com
My advice to women is that if your in a relationship and your spouse cheats on you and you get to find out take a walk out of that relationship because if you don’t and your waiting for him to change he wont.. just last month I found out my husband has been seeing different women with the help of darkhatthacker@gmail.com I was able to read and listen to both calls and text messages without going close to his phone that was how I found out my husband was cheating tho he promised to turn a new leave I accepted and let it go just last week I decided to continue monitoring his phone because darkhatthacker@gmail.com service’s works for a year so I kept on spying and I saw that my husband is still flirting with women. So it’s better to let go than suffer in the hands of a cheating man. Thanks to you darkhatthacker@gmail.com you are great.
ReplyDeleteMy advice to women is that if your in a relationship and your spouse cheats on you and you get to find out take a walk out of that relationship because if you don’t and your waiting for him to change he wont.. just last month I found out my husband has been seeing different women with the help of darkhatthacker@gmail.com I was able to read and listen to both calls and text messages without going close to his phone that was how I found out my husband was cheating tho he promised to turn a new leave I accepted and let it go just last week I decided to continue monitoring his phone because darkhatthacker@gmail.com service’s works for a year so I kept on spying and I saw that my husband is still flirting with women. So it’s better to let go than suffer in the hands of a cheating man. Thanks to you darkhatthacker@gmail.com you are great.
ReplyDeleteI was with my wife in the same room and a call came into her phone but she refused the call, that she would call the person back not until I broke into her phone with the help of russiancyberhackers@gmail.com To know the person calling her and I found out it was a man, With that same number that called my wife russiancyberhackers@gmail.com ran a test on the number and we found out the person has been in contact with my wife for 4 years and am just getting to know. Never feel hackers are not important, they are very important most especially in cases like this..
ReplyDeleteSpecial thanks to (hackingsetting50@gmail.com) for exposing my cheating husband. Right with me i got a lot of evidences and proofs that shows that my husband is a fuck boy and as well a cheater ranging from his text messages, call logs, whats-app messages, deleted messages and many more, All thanks to
ReplyDelete(hackingsetting50@gmail.com), if not for him i will never know what has been going on for a long time.
Contact him now and thank me later.
Special thanks to (hackingsetting50@gmail.com) for exposing my cheating husband. Right with me i got a lot of evidences and proofs that shows that my husband is a fuck boy and as well a cheater ranging from his text messages, call logs, whats-app messages, deleted messages and many more, All thanks to
ReplyDelete(hackingsetting50@gmail.com), if not for him i will never know what has been going on for a long time.
Contact him now and thank me later.
Special thanks to (hackingsetting50@gmail.com) for exposing my cheating husband. Right with me i got a lot of evidences and proofs that shows that my husband is a fuck boy and as well a cheater ranging from his text messages, call logs, whats-app messages, deleted messages and many more, All thanks to
ReplyDelete(hackingsetting50@gmail.com), if not for him i will never know what has been going on for a long time.
Contact him now and thank me later.
For Pooja Room (Mandir), the Northeast direction (Ishaan-kon) is the most suitable place in the home. If you want to build a Pooja Room in a city, village, in a factory, or in a big place, then you can build a Pooja Room in Brahmasthan besides North direction, here we can also keep Pooja Room open from the top.
ReplyDeleteA Vastu Shastra for bedroom provides a feeling of protection because while sleeping, you are not conscious & aware of your surroundings. Principles of Vastu for Bedroom lead us about Directions, Shapes, Colors, Areas of Bed in the Bedroom, etc. for more details https://www.askacharya.com/
ReplyDeleteHave been out of the country for 2 years and I keep getting calls from neighbours that they see my wife with a particular guy on a regular but I don’t believe anything people tell me without seeing it and again I trust and love my wife 100% so I got to forget about it few days the whole thing came to my head again that made me search for a hacker who could help me remotely. behold I found a hacker named jeajamhacker I found this hacker attractive by his services because I read a lot of testimonies about his services so I emailed jeajamhacker@gmail.com to do this job for Me, less than an hour I got full informations of my wife iPhone 12 pro, starting from her WhatsApp messages, call logs, text messages, Instagram, Facebook messenger, icq and so on I read all that she has on her phone and I found out that my wife has a sugar boy she sleeps with and also pays him huge amount of money. Am disappointed in this woman, I trusted her with my life loved and care about her I gave her everything she ever wanted only for me to see that she is cheating on me. thanks to you jeajamhacker@gmail.com this has really thought me never to trust a woman never❌❌
ReplyDeleteWhen it comes to spyexpert0@gmail.com I don’t joke with them they are the best when it comes to GPS tracking, I used them last week to monitor my husband movement, I was able to see were and were my husband goes too on my iPad… so for this I want to say a big Thank you to spyexpert0@gmail.com
ReplyDeleteIf you don"t mind proceed with this extraordinary work and I anticipate a greater amount of your magnificent blog entries
ReplyDeleteBest Data Science courses in Hyderabad
I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting (smithhackingcompanyltd@gmail.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with$50,000,000.00 so i requested for one & paid the delivery fee to obtain the card, after 24 hours later, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via: smithhackingcompanyltd@gmail.com or WhatsApp +1(360)6370612
ReplyDeleteI needed a clean and perfect WhatsApp hacking guess what? I found the best (anonymousmaskhat@gmail.com)
ReplyDeleteI just have to introduce this hacker that I have been working with him on getting my credit score been boosted across the Equifax, TransUnion and Experian report. He made a lot of good changes on my credit report by erasing all the past eviction, bad collections and DUI off my credit report history and also increased my FICO score above 876 across my three credit bureaus report. Email him here via Email him here via hackintechnology@cyberservices.com or whatsapp Number: 213 295 1376.
ReplyDeleteI just have to introduce this hacker that I have been working with him on getting my credit score been boosted across the Equifax, TransUnion and Experian report. He made a lot of good changes on my credit report by erasing all the past eviction, bad collections and DUI off my credit report history and also increased my FICO score above 876 across my three credit bureaus report. Email him here via Email him here via hackintechnology@cyberservices.com or whatsapp Number: 213 295 1376.
ReplyDeleteVastu Consultant Near Me. Why Choose MR. Abhi Kumr Ji! Best Vastu Consultant in Delhi
ReplyDeleteAbhi Kumr is the founder of Divine Gyaan. He is a well-known Author, Entrepreneur, Vastu Consultant & Numerologist. He has been giving consultation services for the last couple of years. And also teaching students about the method and practices which help them to be great Vastu and Numerology experts. Our course helps you to be an expert who gives the best solution to the customers.
Hence, this blog is all about how to apply for Dubai Visa online? Peps, do know first, that Dubai is not accepting any other kind of visa except Dubai e-visa/ document visa. So, one should have to go through with the pre-applied Dubai visa online process to gain his/her visa. Processing time depends on your Dubai visa type but it will hardly take, 6-7 days to proceed.
ReplyDeleteDubai Visa
Special thanks to (hackingsetting50@gmail.com) for exposing my cheating husband. Right with me i got a lot of evidences and proofs that shows that my husband is a fuck boy and as well a cheater ranging from his text messages, call logs, whats-app messages, deleted messages and many more, All thanks to
ReplyDelete(hackingsetting50@gmail.com), if not for him i will never know what has been going on for a long time.
Contact him now and thank me later.
My husband has been acting strange to me so many things going wrong which I could not pick point were the problem is coming from though I tried accessing my husband phone directly but I could not get in because of the Security on his phone, my husband comes home late does not eat my food so many things going on till I came in contact with darkhatthacker@gmail.com after my contact with this hacker I got all I wanted starting from his cell phone behold I found out why my husband has been misbehaving when it comes to me. I found out my husband is having a secret affair with his secretary he gives her so much attention and lost attention for me well thanks a lot to darkhatthacker@gmail.com
ReplyDeleteI curious more interest in some of them hope you will give more information on this topics in your next articles.
ReplyDeletedigital marketing courses in hyderabad with placement
ReplyDeleteAre you willing to know who your spouse really is, if your spouse is cheating just contact hackingsetting, He is good at hacking into cell phones,changing school grades and many more. This great hacker has also worked for me and my colleagues and we got results of our spouses whatsapp messages,call logs, text messages, viber, kik, Facebook, emails, deleted text messages and many more, this hacker is very fast, cheap and affordable. He has never disappointed me and my colleagues for once, contact him if you have any form of hacking problem, am very sure he will help you out. THANK YOU.
contact: hackingsetting50@gmail.com
You have done a amazing job with you website
ReplyDeleteartificial intelligence course in pune
Hi everyone, I’m just giving this big chance to anyone that might need the help of this perfect ethical hacker who rescued my 9years relationship by revealing my husband infidelities through his WhatsApp, gmail, facebook, phone text messages, all call logs and making me know the next step to pursuit after discovering that dark side of the relationship without touching his phone...His charges is affordable, contact him at welcometomydarkworld4@gmail.com thank me later.
ReplyDeleteSo much to write about darkhatthacker@gmail.com which if I start I will cover the whole internet with the good jobs this hacker has done for me so far but right now all I can say to darkhatthacker@gmail.com is I will forever be grateful to you, you really saved me from sudden heart break from my spouse but with your services I found out right on time before my spouse could execute his plan with his side chick
ReplyDeleteIn most cases people fail In one way or the other either trying to spy at there spouses phone or trying to get good school grades but in my own case I don’t fail because I work with the best who has results for me all the time when ever I have problems be it hacking of cell phones or getting the best school grades ever thank you russiancyberhackers@gmail.com for always being the best to me and the world.
ReplyDeleteactual window mangaer crack
ReplyDeletewifi password hacker app download
hack app data pro apk
Native Instruments Absynth Crack 5
Hy2rogen Make It Slap Crack
typing master 10 crack
DS-10 Drum Shaper
toontrack ezdrummer
ozone dynamic eq
kontakt 5 free download crack